Policies, Regulations and Rules
To protect university assets, OIT S&C develops and publishes the following types of documentation to assist the campus community with meeting compliance obligations:
NOTE:
At NC State University, information security standards are developed and published as rules.
About PRRs
OIT S&C develops PRRs working collaboratively with all campus IT representatives. Upon final approval, OIT S&C then works with the Office of General Counsel (OGC) to publish the PRRs in the Information Technology category of the university’s Policies, Regulations & Rules (PRR) website.
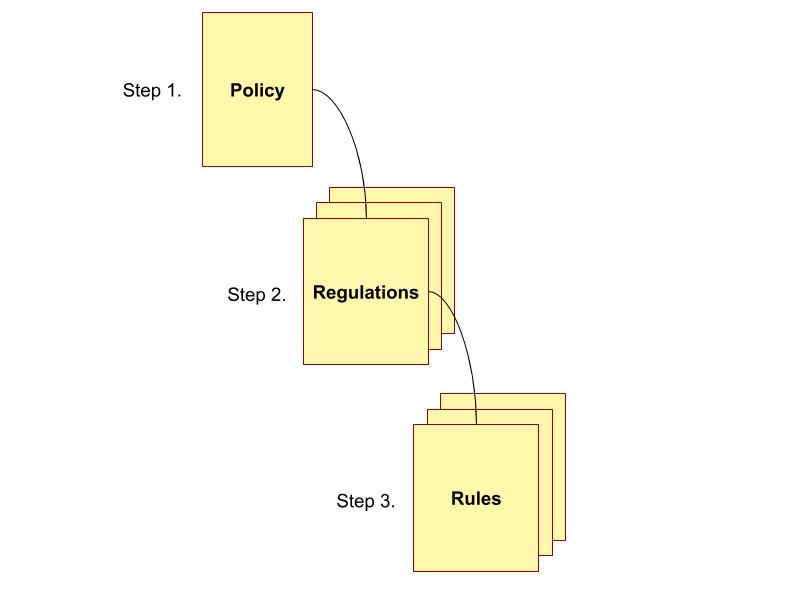
As shown in Figure 1, before establishing any regulations or rules, a policy must exist. Regulations support the policy with details about general applicability, while rules provide details relevant to specific circumstances.
Figure 1. Policies Must Exist Before Creating Regulations (and then Rules and Guidance)
NOTE: After developing and publishing a complete PRR set, OIT develops and publishes supplemental guidance, which typically consists of one or more documents or web pages providing detailed, step-by-step instructions.
See the following sections for details:
- PRR Definitions
- PRR Development
- PRR Review and Approval Process
- Published PRRs
- Supplemental Guidance
PRR Definitions
OIT S&C adheres to the university’s PRR definitions defined in Table 1.
Table 1. PRR Definitions
| PRR Type | Governing Body | Definition |
| Policy | Adopted by the Board of Trustees pursuant to authority delegated by law or the Board of Governors. | Any standard, statement, or procedure of general applicability |
| Regulation | Adopted by the Chancellor or chancellor’s delegee. | Any standard, statement (which may include a policy statement), or procedure of general applicability |
| Rule | Adopted by an academic or administrative unit within the university to implement an NC State University Policy or Regulation; alternately, can address matters within the operational authority of the unit. A Rule may supplement, but not conflict with, policies and regulations. | A standard, statement or procedure, other than a policy or regulation |
PRR Development
In conjunction with all UNC System institutions, and per the Chancellor’s Adoption Letter dated March 2012, NC State University adopted ISO 27002, an internationally recognized framework for information security. The ISO 27002 Security Framework guides the development of OIT S&C PRRs.
PRR Review and Approval Process
After creating or revising the first draft of a PRR, the draft undergoes the review and approval process defined in the following IT PRR Process flowchart (Figure 2) and Table 2:
Figure 2. IT PRR Process Flowchart
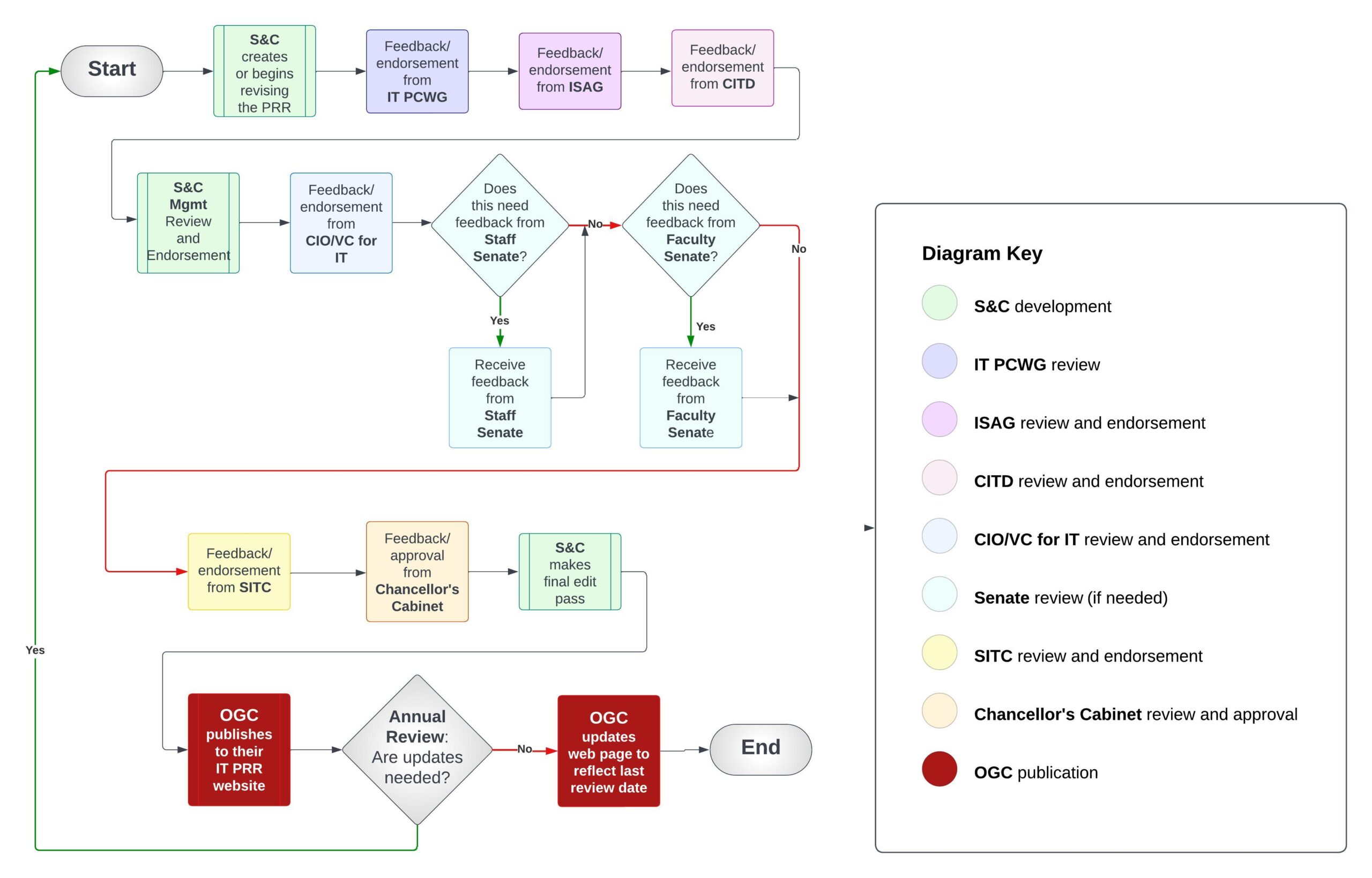
Table 2. PRR Review and Approval Process
| Step | Action Owner | Description |
| 1 | Information Security Advisory Group (ISAG) | Review and endorsement |
| 2 | Appropriate IT governance structure and other committees as needed | Review and endorsement |
| 3 | Chancellor’s Cabinet | Review and approval |
| 4 | Office of General Counsel (OGC) | Publish to PRR website |
Published PRRs
OIT S&C works with the NC State Office of General Counsel (OGC) to publish formally approved PRRs to the university.
IT PRRs are published on the university OGC website under the Information Technology category.
Supplemental Guidance
In addition to publishing PRRs for the protection of university data, OIT provides the supplemental documentation described in this section.
Password Standard
NC State’s password standard complies with REG 08.00.02 (the Computer Use Regulation) to ensure appropriate security protections are in place; defines the password requirements at NC State and applies to anyone accessing the NC State network.
Mobile Device Security
In accordance with the Computer Use Regulation and RUL 08.00.18 — the Endpoint Protection Standard (EPS), the Mobile Security at NC State website provides detailed procedures to secure the mobile devices, data, and wireless connections of all campus members who use them to access university data. These guidelines apply to university personnel using mobile devices to access any university data, including email. In addition, these guidelines help secure that data should a device become compromised, lost, or stolen.
Technology for Travel
The Technology for Travel page provides requirements and tips for securing mobile devices before, during, and after traveling. When you travel with a laptop, tablet or smartphone, the risk of loss and theft are so much higher — losing not only your device but also the data it stores.
Please note it is impossible to protect mobile devices against every form of data breach; however, the more you do, the safer you are.
EPS Guidance
The EPS Guidance page helps IT support staff comply with security requirements per RUL 08.00.18 — the Endpoint Protection Standard (EPS). All IT groups are responsible for complying with said EPS requirements per their areas of responsibility.
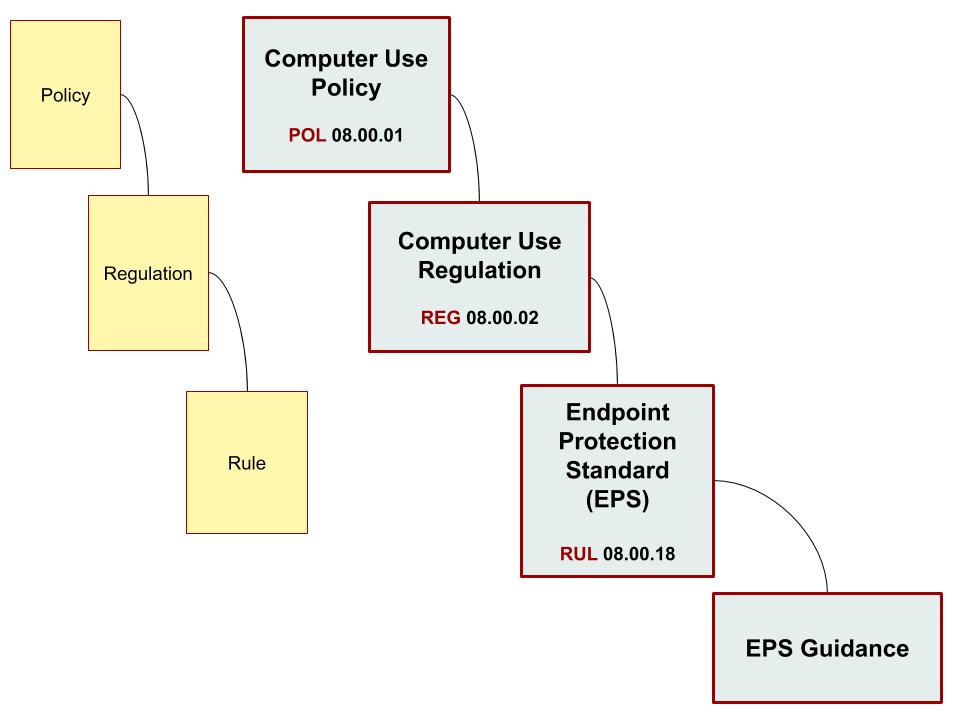
Example of PRR and Guidance
Figure 3 shows how RUL 08.00.18 — the Endpoint Protection Standard (EPS) and the EPS Guidance page correlate to the earlier PRR hierarchy figure.
Figure 3. Example of PRRs and Guidance